Identity and Access Management

Table of contents
Identity and Access Management
Modular Best Practice Solution for Establishing an Integrated IAM Solution for SME
Today, organizations use a complex system of IT solutions that combine traditional on-premise solutions, clouds or hybrid models. The growing number of users is rapidly increasing the volume of data. Employees need access to these data, but so do partners and customers. The automated withdrawal of IT authorizations must be given special consideration, for example when an employee leaves the company. In addition, regulatory requirements such as TISAX, ISO 27001, SOX and SAS70 are increasingly being tightened in the direction of audit-proof management of identities and access rights.
To ensure compliance with regard to data protection, identity and access management must be traceable, detailed and efficient.
We support you in implementing the optimal solution for your Identity and Access Management (IAM). Through our modular best practices in connection with OpenIAM, we cover all IAM aspects and simplify the management of roles and identities while increasing the productivity of your employees.
Trust our many years of experience in cybersecurity and IT. Our proven, innovative solutions are used worldwide.
Learn more about your IAM solution now!
Establish Efficient IAM Solutions with a Modular Best Practice Approach

Manage access securely
Automate your access and identity management and improve your IT security with a comprehensive software solution. You will benefit from extensive savings of resources, as there will be less error-prone manual activities, and because processes are standardized. At the same time, the system still offers ample flexibility to adapt to your goals and to the interfaces you use. Furthermore, the ease of use and the self-service portal with its many features sustainably increase the productivity of your employees.
Modular structure
The best practice modules are structured in such a way that a base module (Automation of the User Life Cycle) is required as a foundation. Based on this base module, our customers can acquire additional modules as needed (e.g., Ordering / Self Service, Recertification or Web Access Management). The modular approach gives our customers the opportunity to upgrade the established solution in economical smaller steps, phase by phase and module by module.
Use of standards
To configure your individual IAM solution, the complex functions of an Identity Access Management / Identity Access Governance solution are divided into small, self-contained and therefore cost-effective modules. Customization and content of the modules are based on best practices of TUV Rheinland i-sec GmbH. As standards, in addition to the required pre-configurations they also contain organizational documentation such as interface agreements or process descriptions. They contain the processes for hiring, transferring or delimiting employees.
Shortened Selection Process
There is a clear definition of the qualitative and quantitative content for the modules, which can be supplemented according to customer needs. We begin by conducting a one-day workshop and together with the client determine which best practice modules are required and how they should be tailored.
A Software for an Integrated Identity and Access Management
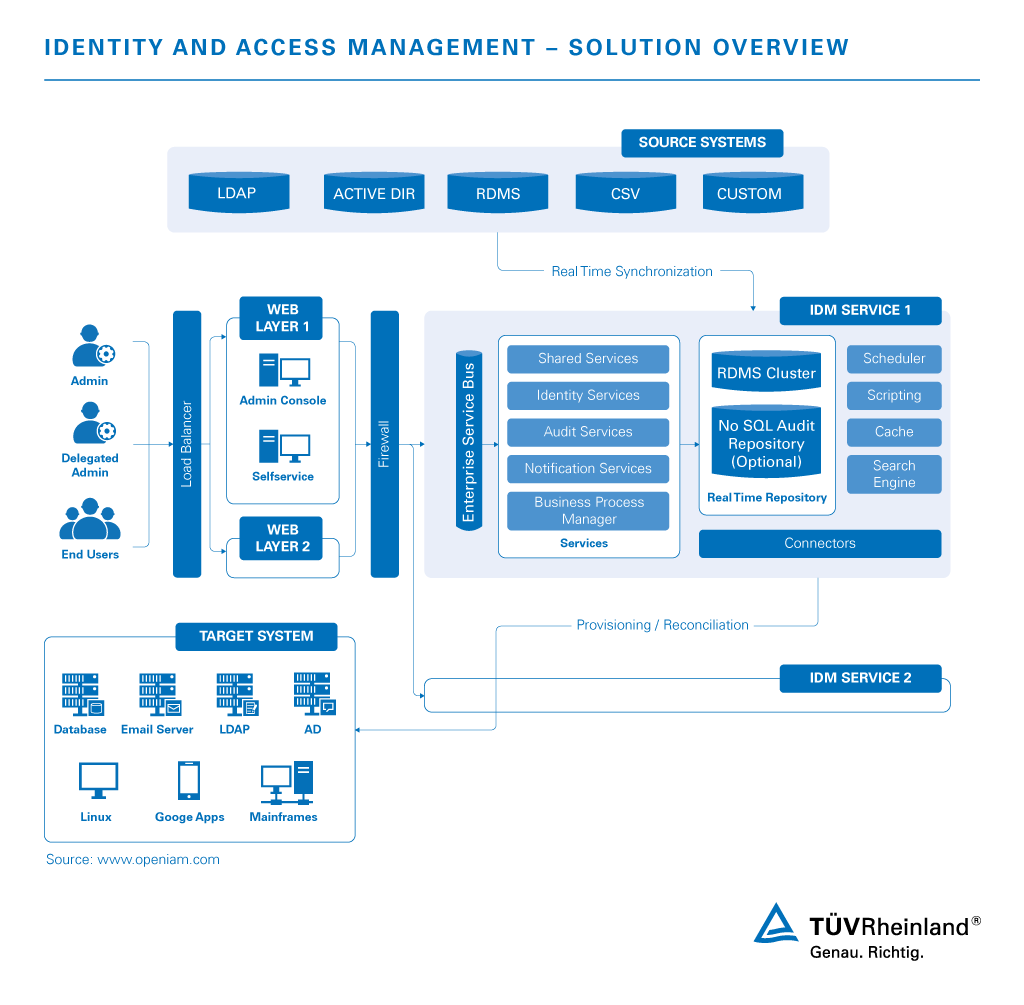
Automated Provisioning and User Identity Lifecycle Management
During operation, employees must be ensured to have the required authorizations within all systems at all times. But it is equally important to be able to revoke access when needed. An automated solution provides effective and tamper-proof support for managing access rights in the event of hirings, resignations, promotions or changes in project management.
Access Request
Via a user-friendly self-service approach, employees can access the service catalog and easily request authorizations, which are then approved automatically through predefined processes. Every step is logged, so organizations can track how and when access was granted.
Periodic Review and Access Certification
Thanks to the included access review and certification campaigns, organizations can ensure that users have appropriate access rights and that incorrect authorizations are corrected on a regular basis. The Access Certification solution provides an easy way to define the review workflow, so progress can be monitored and deadlines can be met.
Role Management
Role Based Access Control (RBAC) allows technical and business roles to be defined. The role model is used in conjunction with automated provisioning to ensure that the correct level of access is granted in a consistent manner.
Access Manager
The integrated Access Manager of our software provides a scalable, secure and consistent solution for accessing applications in all environments using the following tools:
We Are Your Trusted Partner
Trust the expertise of our experts and the reliable software solution by our partner OpenIAM when implementing your Identity and Access Management. Through years of experience in the implementation of cybersecurity projects and the application of proven standards, we have developed a modular best practice solution for you. This allows us to implement your customized IAM solution in a timely manner. We assist you from planning to implementation to the support during ongoing operation.
Would you like to benefit from an efficient access and identity management? Request your customized quotation!
FAQ: Answers to Your Questions about TUV Rheinland’s IAM Solution
Are you interested in our modular best practice solution for Identity and Access Management, but still have questions? Our experts have summarized the answers to frequently asked questions for you. Don't hesitate to contact us if your question has not been answered.
Our Sustainability Initiatives
Nothing less than the future is at stake. Companies, institutions, public authorities and each and every one of us can play a positive role in shaping the path to tomorrow. We provide you with comprehensive support to ensure that you operate safely, sustainably and efficiently for many years to come.
Contact your IAM expert now!






